Such personal and sensitive information in the wrong hands could be used against you, or put you and others at risk, whether or not you have anything to hide. So how do you know for sure if there’s spyware on your smartphone or computer? We’re going to show you the telltale signs to be aware of, how to check for spyware and recognize what you find, plus spyware removal tips to get it off your device.
Signs That Your Computer Or Phone Has Spyware
Spyware software is designed to log everything a computer or phone does and sends out usage data while remaining undetectable. Some examples of spyware are keyloggers, which monitor and record key presses on your computer’s keyboard, or take screenshots of your device. If you have an eerie feeling that you’re being watched or someone’s listening in on your phone conversations, or you have a compromised device, these signs should ring the alarm bells. It’s time to explore your spyware removal options.
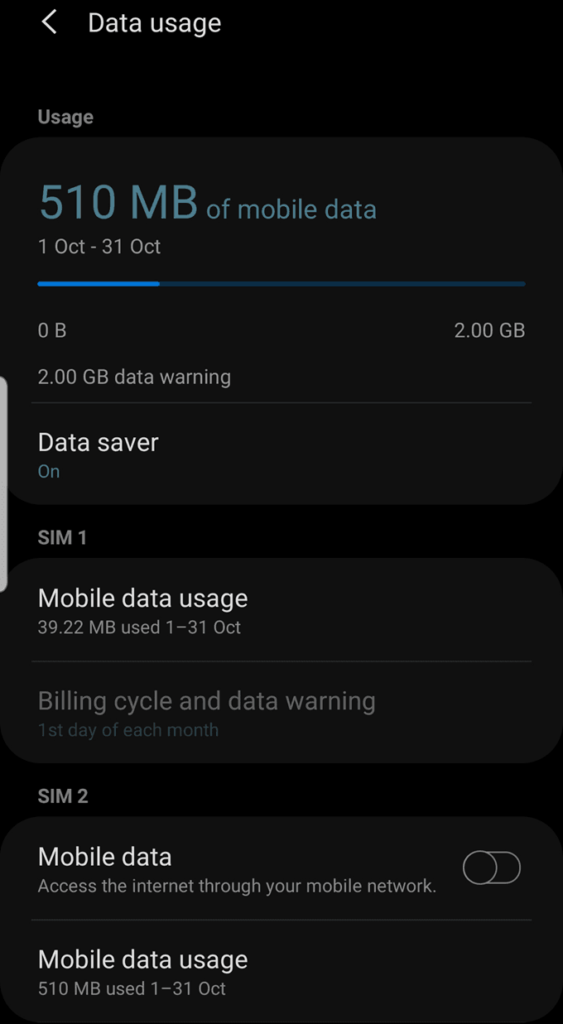
Excessive Data Usage
Spyware consumes a significant amount of resources and network bandwidth when installed on your computer or phone. If you notice your monthly data usage is abnormally high, there’s a decent chance spyware was installed on it. This happens because the software uses data to send out the usage data collected from your device. However, high-end spy apps use much less data so it may be impossible to detect that on your data usage overview.
Sudden Drop In Battery Life
This is another indicator of spyware on your computer or phone. If you notice that your battery runs out of juice at an unusually high rate, it could be the presence of spyware that’s draining it, especially if it records through your speaker or camera. If your phone has a removable battery, you can test with different batteries first, because you could also have an old one that drains out quickly.
Slow Performance
There are several reasons for slow speeds on a computer or phone, like if your storage is full, or the device hardware and software isn’t capable of running many apps at a go. However, if you’ve ruled that out, and your device is growing noticeably slower than usual, it’s probably being monitored or remotely controlled.
Difficulty While Trying To Shut Down & Unexpected Reboots
Spyware compromises your device and keeps running in the background, so you may find it hard to completely shut down your computer or phone. Sometimes it could reboot for no obvious reason, or without your input, which is a sign that someone could have remote or unauthorized access to it. Similarly, if you notice your device takes a longer time than usual to close active processes and shut down, the spyware could be the cause as it’s still running actively in the background.
Strange Background Noises During Calls & Odd Text Messages
Back when landlines were in use, it was usual to hear weird background noises as the lines weren’t always stable. Today though, networks have stable connections and strong signals. So if you hear strange clicking sounds, this could mean your phone is being monitored. If you receive unexpected yet odd-looking text messages with strange characters, it’s possible there’s a spyware tool installed on your phone. This is “coded language” the spyware tool uses to communicate to the external party, but also a sign of poor quality spying software.
Abnormal Battery Temperature
Battery temperature could be tied to several technical issues, but if you haven’t had any issues with your battery before and it’s relatively warm, it could be spyware sending out usage data to other devices.
How To Check, Recognize & Remove Spyware Installed on Your Computer Or Phone
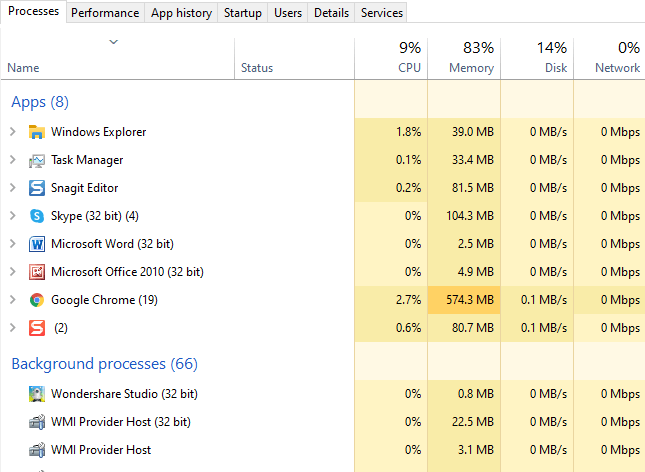
If you have a Windows machine, you can check for spyware through the Start bar to double-check installed program lists. If you don’t see any suspicious programs, press CTRL+ALT+DEL and click Task Manager to see all processes currently running on your computer and identify any suspicious programs.
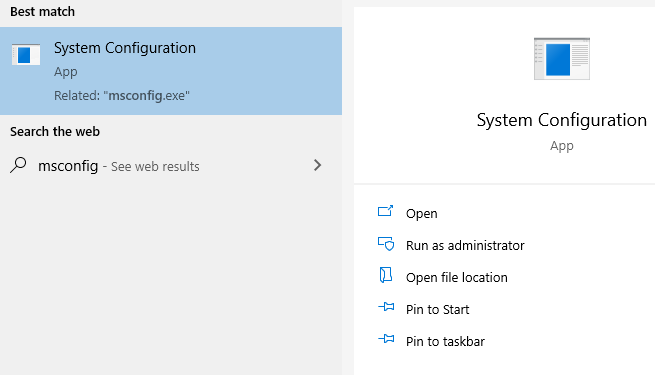
Alternatively, use MSConfig in the Windows search bar and check for any strange software that is consuming a significant amount of memory. Terminate its process temporarily, or, if you’re not sure what it’s for, search for it online, and remove it from your computer if confirmed malicious.
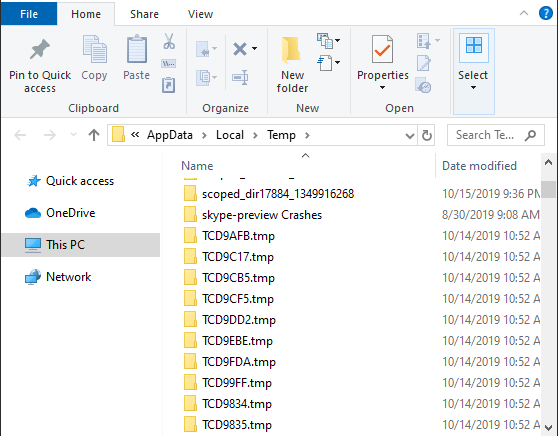
On a Mac, you can click Launchpad, Activity Monitor (or go through Spotlight), and Other to check the current programs running on your machine.Check the TEMP Folder and delete suspicious files. Your computer creates the TEMP folder to pull up a website or program easily, but it holds more than just temporary files – malware often hides here. If you see any suspicious files in this folder, you can delete the specific files or remove everything from the TEMP folder.
Install anti-spyware software. This is the best way to scan your computer for spyware. It deep-scans your computer drives to identify and remove any potential threats lurking within. If you don’t have one, you can try some of the best free spyware removal tools like SUPERAntiSpyware or Malwarebytes.
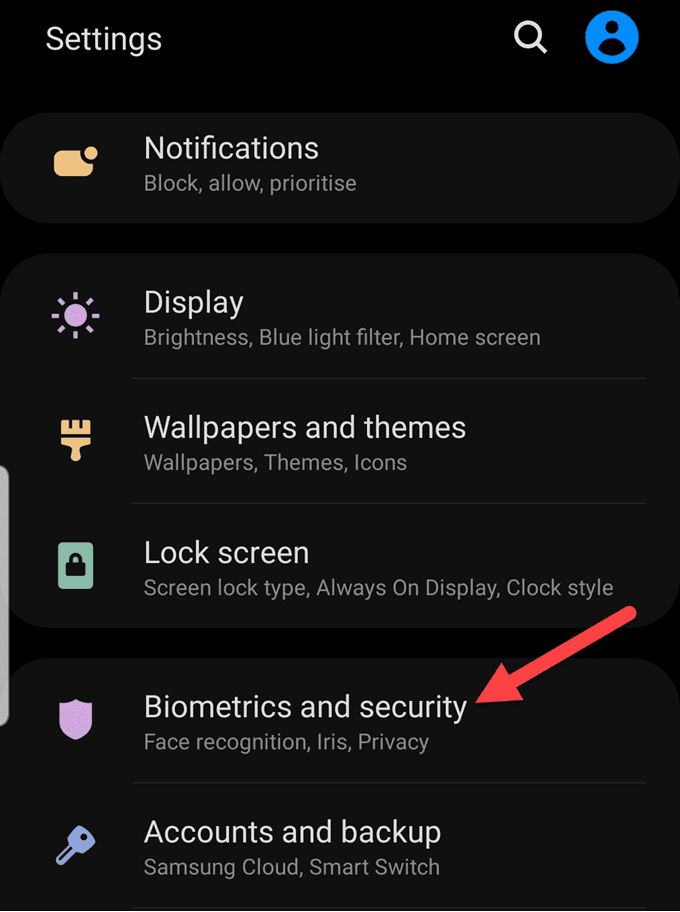
For Android phones, check whether your settings allow unknown sources to download and install apps, as this will happen without your consent. To do this, go to Settings>Biometrics and Security (or Security).
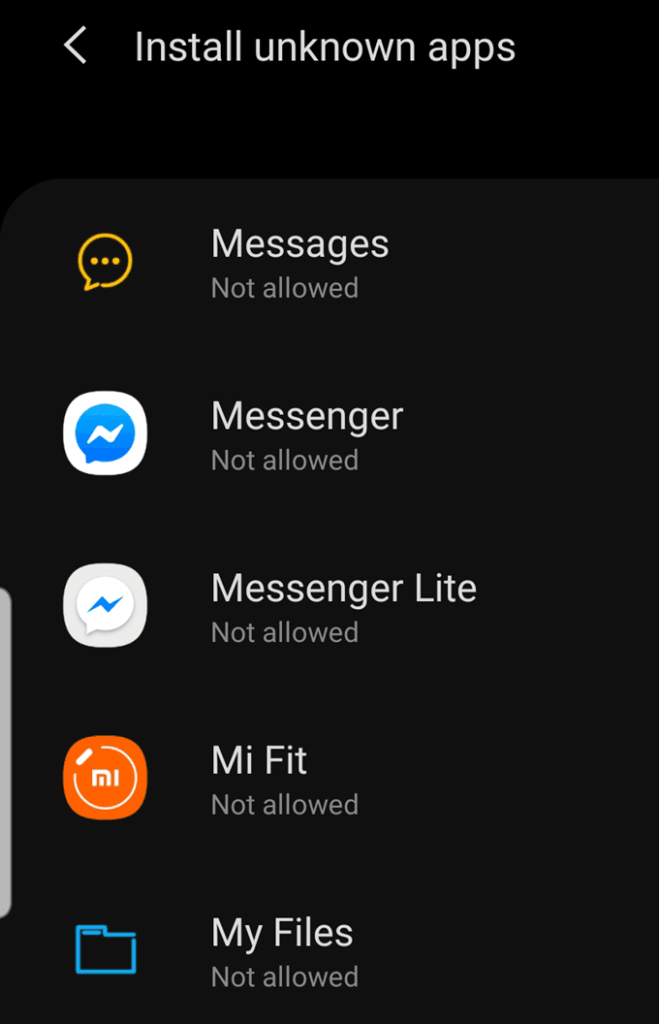
Tap on Install unknown apps (or Allow unknown sources). Check for any suspicious apps that you don’t recognize, though some use generic names to escape detection, and change the app settings to ‘Not allowed’.
If you suspect tampering or jailbreaking, download the Root Checker app from Google Play Store, and it’ll check for jailbreaking.iPhones are much harder to jailbreak or install with spyware or malware, but there are several ways you can determine whether or not your iPhone has spyware.
Note: Not every form of spyware requires a jailbroken device to be installed. If you see an unfamiliar process or app, do a quick search online to see if it’s legitimate or not.
Next Steps
As with most things in life, go with your sixth sense, especially if you suspect something isn’t right, and seize control of the situation.
Once you’ve checked and cleaned your computer or smartphone of any infection, keep an aggressive spyware removal tool and robust security suite for real-time protection.Other things to do include changing your passwords, enabling two-factor authentication, and updating your operating system to the latest version.Contact your financial services provider to warn them of any possible fraudulent activity with your accounts. If your computer or phone holds sensitive business information, make a public disclosure, or report potential violations of state and federal laws to law enforcement authorities.
As a last resort, perform a factory reset on your computer or smartphone. You could also buy a new smartphone or computer and take back control of your right to privacy.